 Overwhelmed by what feels like constant news of data breaches? With headline after headline about companies being breached, it’s easy to feel like it’s out of our control. That’s why it’s more important than ever to know how you can protect your information (and your clients’) from cyber attacks like the ones we’re always hearing about. But how do you accomplish that without stopping Internet use altogether? Although there is no way to prevent a breach entirely, there are plenty of best practices you can employ to significantly reduce their impact.
Overwhelmed by what feels like constant news of data breaches? With headline after headline about companies being breached, it’s easy to feel like it’s out of our control. That’s why it’s more important than ever to know how you can protect your information (and your clients’) from cyber attacks like the ones we’re always hearing about. But how do you accomplish that without stopping Internet use altogether? Although there is no way to prevent a breach entirely, there are plenty of best practices you can employ to significantly reduce their impact.
The Breach Landscape
You may feel that people are making a bigger deal about these breaches than they’re worth, but consider the breach landscape 10 years ago, which you can see in this image from InformationIsBeautiful.net. Each bubble here represents the magnitude of database breaches by the number of records compromised.
Breaches from 2008 to 2010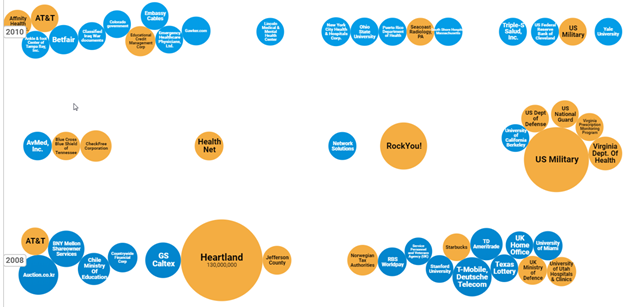
Source: InformationIsBeautiful.net
From 2008 to 2010, we see a few major breaches. But if we look at the past few years, the graph gets a little . . . claustrophobic.
Breaches from 2016 to 2018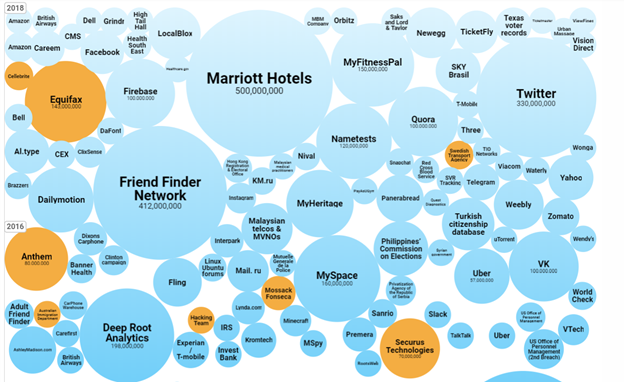
Source: InformationIsBeautiful.net
Trust me, it’s not hype. It’s real. And as consumers of these services, we can’t stop these data breaches from happening. But depending on the breach, it usually takes only a couple of key actions to reduce how you’ll be affected, if at all.
The Breach Game Plan
No breach is the same; there is no list of the “top three ways” to reduce impact across the board. Can the same steps be followed when your bank, your pizzeria rewards club, or your fantasy football service gets hacked? Absolutely not.
The secret lies in pinpointing the specific information that’s at risk. Ask yourself, if attackers were to get ahold of this account, what could they access? From there, you can devise a simple game plan for almost any breach. Getting in this mind-set will help you as a consumer, but you can also impart this invaluable wisdom to your clients.
Credit and debit card information. We can always be safer with how we use our credit and debit cards, such as by entering payment information online only at HTTPS sites (as opposed to HTTP), never storing payment information on sites, and doing business only with companies we trust. But even so, our payment information will get out there, considering the amount of online shopping we do.
After catching wind of any breach of credit or debit card information, it’s best to:
- Review your recent activity to see if any unauthorized charges occurred.
- Report any unauthorized charges to your bank or credit card company.
- Request a replacement card.
It’s also important to note that not all data breaches are properly disclosed—and many are disclosed months (or even years) after the compromise took place. Get in the habit of regularly monitoring your financial activity, and report anything suspicious as soon as you can.
Passwords. In the past few years, we’ve learned that LinkedIn, Yahoo, and Twitter passwords were all exposed on a mass scale. What should you do when something like this happens again? Change your password, but also ask yourself, Have I used this password or a similar password for other online accounts?
Even if you have the strongest password of all time (if such a thing could exist), if you use it in multiple places—and one of those places is breached—someone could access all accounts that use that password. Think about the benefits of breaking this “password reuse” habit. Next time an incident happens, all you would have to do is change that one breached site’s password. Adopting a password manager is one way to simplify this process.
Enabling multifactor authentication can also help protect your account behind an additional layer of security—like a smartphone or e-mail notification every time you use your password. So, if your password were exposed, an attacker would still need that other form of authentication to log in, which he or she is unlikely to have.
Social security number. Unlike a password, you can’t change a social security number and call it a day. What you can do is freeze your credit. As of September 2018, freezes are free, and they’re the most heavy-duty tool at your disposal for protecting your credit. It’s a preventive measure against (1) new lines of credit being opened in your name and (2) hard inquiries.
Some other tools worth looking into for an exposed social security number include:
- Fraud alerts: These encourage companies to verify with you before opening new lines of credit.
- Credit monitoring: These tools monitor your credit in real time for any changes. These are reactive and not proactive; they alert you after the unauthorized activity happens.
- Identity theft protection services: For a hands-off approach to identity protection, these products offer tools and resources for one subscription fee.
Putting the Formula into Practice
Let’s apply what we’ve learned to a breach that doesn’t fit so cleanly into these categories: the 2018 Facebook breach.
First, some background: Facebook discovered a weakness that allowed attackers to take over any account. Attackers could find and reuse anyone’s unique access token, allowing them to authenticate users’ accounts. There was no known evidence of misuse, only the potential for it. Affected accounts were notified by Facebook via e-mail.
If you received such a message today, what would you do?
Making your own to-do list. Again, ask yourself: What does this account have access to? With social media specifically, the answer depends on how you use your account.
- Does your profile have your real birth date?
- What third-party applications do you have connected to your Facebook account?
- Do you use Facebook Connect to log in to other online accounts—ones that might store your payment information?
- Have you ever messaged a family member your Netflix password, credit card information, or even social security number?
Without the impossible one-size-fits-all list for remediating such a breach, I hope this line of thinking can help you create your own list. Once you identify what’s at stake, what steps do you take to lock it down? Can you separate those connected apps—or at least change their passwords? Do you need to limit the type of information you post on Facebook? Can you monitor anything else that may have been exposed, like a credit card number?
Will You Be Ready for the Next One?
When news of another breach hits the headlines, there’s no need to panic, but there is the need to take action. Getting in the mind-set we’ve laid out here can help you be proactive without going overboard. If a breach does affect you personally—to the point where someone is abusing your information and you can’t figure out what to do next—we recommend checking out the helpful resources at IdentityTheft.gov.
Have you or your clients experienced any data breaches in the last few years? What steps did you take to protect your information again? Were you able to help your clients? Please share your stories below.



 Print
Print


